A recent malware discovery has many of us security pros very concerned: rootkits targeting embedded devices. The discovery is a rootkit called Rootkit.TmpHider that came with a trojan that infects systems via USB drives. This in itself is not all that concerning, what *is* very concernful is that the driver files that make up the rookit have a legitimate digital signature from....wait for it...an embedded device maker
Realtek. Worse it appears to targeted at SCADA control systems.
Not good.
Several are discussing this new trojan that has rootkit technologies built into it:
Wilders Security,
The H-Security site,
The Elder Geek.
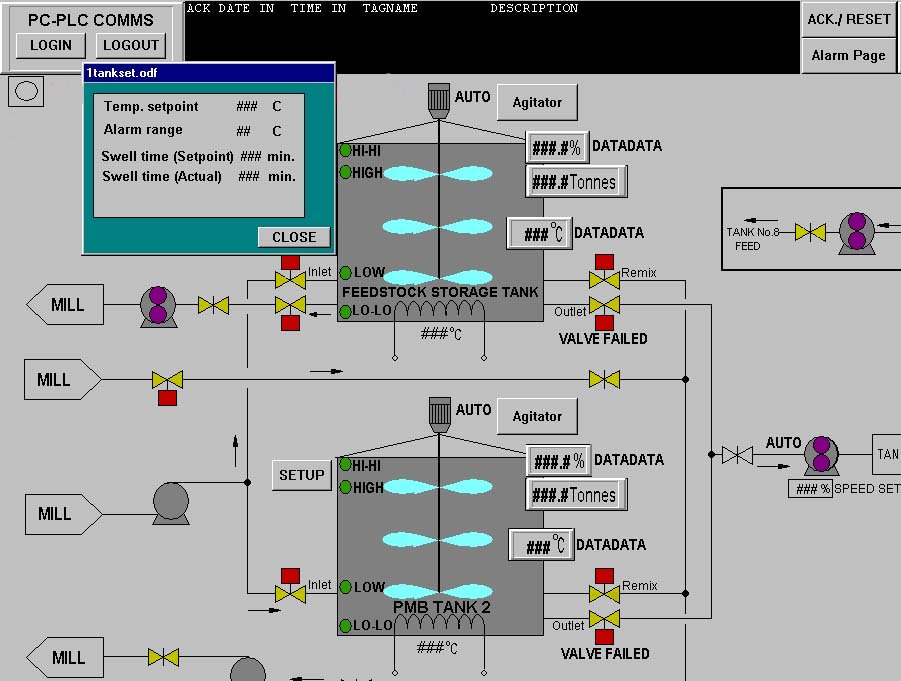
Why are we concerned you ask? These embedded devices are everywhere controlling everything including critical systems such as water system, power grids, etc. AND in a
scary finding made by malware analyst Frank Boldewin of
www.reconstructer.org, this rootkit has database queries that target
WinCC SCADA systems by Siemens. That's bad news.
To add to this concern is the fact that these devices rarely get updated, if at all, so all bugs and vulnerabilities that existed when they were designed still exist. Furthermore, the trust model in these devices is usually quit open, making it very easy for worms to propagate.
Here's hoping that new embedded systems have stronger security built into them.